1. Install greasemonkey plugin for firefox
https://addons.mozilla.org/en-US/firefox/addon/greasemonkey/
2. Install cookie-injection-plugin for greasemonkey
http://userscripts.org/scripts/show/119798
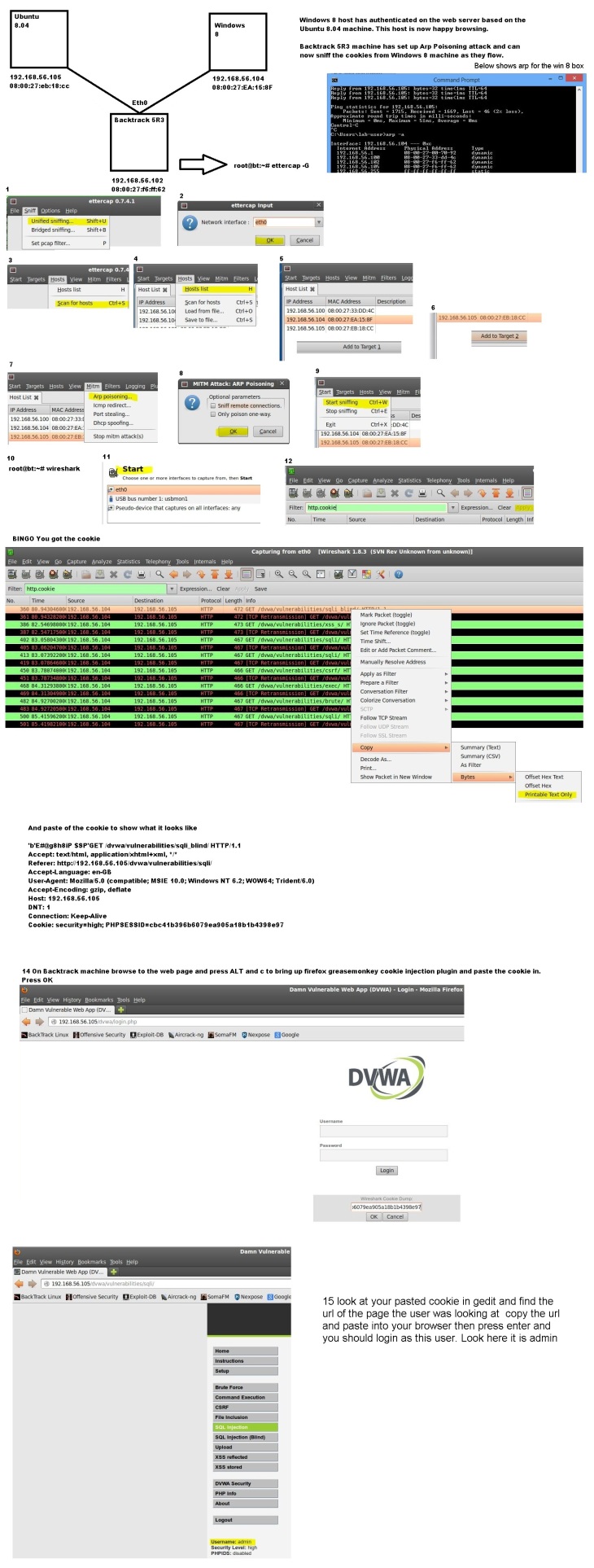
3. Wireshark is required to collect a cookie. (This would typically be done by placing your self as the Gateway via man in the middle attack)
To start wireshark in backtrack
root@bt:~# wireshark
Then select your interface and start. In the filter box type in http.cookie and apply.
When you start seeing get statements you are ready to copy the cookie
38 10.927591000 192.168.56.101 192.168.56.103 HTTP 509 GET /dvwa/vulnerabilities/sqli/ HTTP/1.1
4. Cookie Copy.
Right click and high-lite your chosen wireshark sniff Copy / Bytes / Printable Text Only
This will copy the cookie now paste it into gedit it should look something like the below.
”[EP@@8g8ePsH’=O
sZqGET /dvwa/vulnerabilities/sqli/?id=&Submit=Submit HTTP/1.1
Host: 192.168.56.101
User-Agent: Mozilla/5.0 (X11; Linux i686; rv:14.0) Gecko/20100101 Firefox/14.0.1
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip, deflate
DNT: 1
Connection: keep-alive
Referer: http://192.168.56.101/dvwa/vulnerabilities/sqli/
Cookie: security=low; PHPSESSID=90d6a50f462bcf2c4806d392669753a2
5. To start greasemonkey enable it on your browser (Right top courner) Go to the url in question http://192.168.56.101/dvwa/ and you should see login page. Refresh to prove you cant login.
Then press Alt + C this will open greasemonkey Wireshark Cookie Dump box and paste in your copped cookie and press ok.
6. In the captured cookie look at the url that the client was on and paste this in. From my collected cookie above I would paste in http://192.168.56.101/dvwa/vulnerabilities/sqli/
Then press enter and if the site is vulnerable to weak cookie authentication you will have logged in with the clients authentication and have there same rights!
——————————————————-
Changes required to run ettercap
root@bt:~# gedit /etc/etter.conf
[privs]
ec_uid = 65534 # nobody is the default
ec_gid = 65534 # nobody is the default
Change to
[privs]
ec_uid = 0 # nobody is the default
ec_gid = 0 # nobody is the default
# if you use ipchains:
#redir_command_on = “ipchains -A input -i %iface -p tcp -s 0/0 -d 0/0 %port -j REDIRECT %rport”
#redir_command_off = “ipchains -D input -i %iface -p tcp -s 0/0 -d 0/0 %port -j REDIRECT %rport”
Change to
# if you use ipchains:
#redir_command_on = “ipchains -A input -i %iface -p tcp -s 0/0 -d 0/0 %port -j REDIRECT %rport”
#redir_command_off = “ipchains -D input -i %iface -p tcp -s 0/0 -d 0/0 %port -j REDIRECT %rport”
Save
root@bt:~# ettercap -G
Below screenshot showing how to perform
It’s much easier to use Burp Suite for this sort of thing
Hi Jungef, thanks for reading. Your right but I don’t have much experience with burp. You got a blog or any way of showing us all how you do it in burp. Happy to link to a blog of yours if like.